What is BitLocker and How Does it Work? | ACE Data Recovery Article
Microsoft’s BitLocker encryption will prevent any successful data recovery attempt unless you have the backup key.
In a world increasingly reliant on digital data, ensuring the security of sensitive information is more crucial than ever. BitLocker, a feature developed by Microsoft, stands as a robust solution for protecting your data through encryption. Let's delve into what BitLocker is and how it works, breaking down the complexities into easy-to-understand concepts.
Plan for the worst and hope for the best! If your hard drive needs data recovery, the biggest obstacle in your way might be yourself. Microsoft’s BitLocker encryption will prevent any successful data recovery attempt unless you have the backup key. Make sure you have it secured!

What is BitLocker?
BitLocker is a disk encryption program designed to enhance the security of your data by encrypting entire disk volumes. This includes your operating system drive, external drives, and other fixed or removable storage devices. Essentially, BitLocker scrambles the data on your disk, making it unreadable without the appropriate key.
How Does BitLocker Work?
- Encryption Process: When you enable BitLocker on a drive, it initiates the encryption process. BitLocker uses a symmetric key algorithm, typically Advanced Encryption Standard (AES), to encrypt the entire content of the chosen drive. This means that the same key is used for both the encryption and decryption processes.
- Key Generation and Storage: BitLocker generates two types of keys during the encryption process: the Full Volume Encryption Key (FVEK) and the BitLocker Volume Master Key (VMK). The FVEK is the key that actually encrypts and decrypts the data, while the VMK is used to protect the FVEK. These keys are, in turn, secured by the BitLocker encryption key, which is derived from either a user-supplied password, a USB key, or a TPM (Trusted Platform Module) if available. The TPM is a hardware component that stores cryptographic keys, adding an extra layer of security by ensuring that the encryption keys are stored locally on the device.
- Authentication: To access the encrypted data, you need to authenticate yourself and provide the necessary credentials, such as a password or a smart card. BitLocker uses these credentials to unlock the TPM-stored keys, allowing the system to decrypt the data on-the-fly as it is read or written.
- Pre-Boot Authentication: BitLocker also offers pre-boot authentication, ensuring that the system remains secure even before the operating system loads. This adds an additional layer of protection by requiring users to enter a password or insert a USB key before the system can access the encrypted drive.

Bitlocker User-Friendly Features:
BitLocker is designed with user-friendliness in mind. Once it's set up, users often don't even notice its presence. File access and data modification occur seamlessly in the background, with the encryption and decryption processes handled transparently by the system.
Windows 11 Pro and BitLocker Encryption
Windows 11 Pro takes a proactive stance on security by automatically enabling the software version of BitLocker during installation, leaving users with no apparent option to opt out. Encrypting your storage drive offers significant protection against theft, making it particularly beneficial for laptops. In the event of a security breach where a thief gains physical access to your computer and cannot boot into Windows, they may resort to removing the SSD, connecting it to another computer, and attempting unauthorized data access.
Verifying Drive Encryption Status
- Launch an elevated command prompt (run CMD as an admin).
- Enter the command:
manage-bde -status.
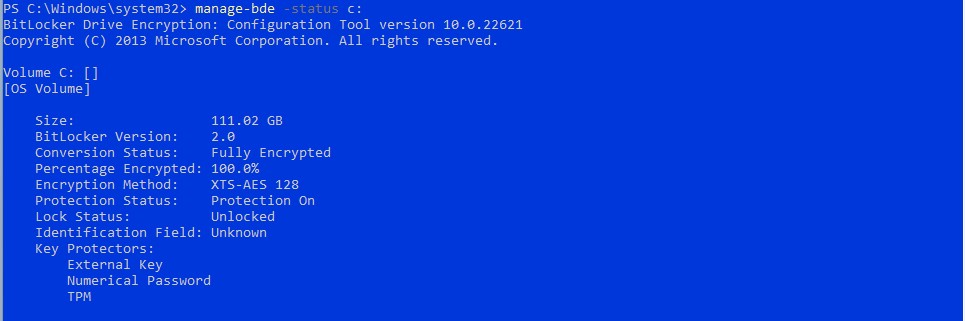
If the drive is encrypted and the thief lacks the encryption key, access is denied. However, if it's not encrypted, using any SSD enclosure can turn it into an external storage drive, providing full access to your files. Windows 11, when paired with Intel TPM, streamlines BitLocker without requiring a password at boot time. However, in the event of a computer failure, the TPM chip becomes inaccessible, necessitating the BitLocker recovery key.
Manufacturer Policies and Default Installation
Major computer manufacturers like Dell, HP, and Lenovo confirm shipping systems with Windows 11 Pro featuring software-based encryption. It's likely that other OEMs follow similar policies. Those installing Windows 11 Pro from scratch may encounter default software-based encryption. Still, compatibility issues persist, with some motherboards not meeting Microsoft's requirements due to factors like local accounts, lack of network during installation, improperly configured Secure Boot, or other BIOS options.
BitLocker Recovery Key Retrieval
BitLocker typically ensures that a recovery key is safely backed up before activation. Recovery keys may be found in several places, depending on user choices during BitLocker activation:
BitLocker Recovery Key Retrieval
BitLocker typically ensures that a recovery key is safely backed up before activation. Recovery keys may be found in several places, depending on user choices during BitLocker activation:
- Microsoft Account: Visit Microsoft Account Recovery on another device.
- Printout: Check for a printout made during BitLocker activation.
- USB Flash Drive: Plug it into your locked PC and follow the instructions. If saved as a text file, use another computer to read it.
- Work Account: If your device was signed into an organization using a work email account, the recovery key may be stored in the organization's Azure AD account. Access it directly or contact IT support.
- System Administrator: For devices connected to a domain (usually work devices), ask the system administrator for the recovery key.
Important Reminder: If you can't locate the BitLocker recovery key and can't undo configuration changes, resetting your device is the only option. This will remove all files. Microsoft support cannot provide or recreate lost BitLocker recovery keys.
Complexity to recover corrupted data from BitLocker encrypted drive
Recovering corrupted data from a BitLocker-encrypted drive can be a challenging task due to the robust encryption mechanisms in place. BitLocker employs strong encryption algorithms and security features to protect data, making it difficult for unauthorized parties to access or recover information. Here are some key factors contributing to the difficulty of recovering corrupted data from a BitLocker-encrypted drive:
- Encryption Strength: BitLocker typically uses strong encryption algorithms, such as Advanced Encryption Standard (AES) with 128 or 256-bit keys. This level of encryption provides a high degree of security, making it computationally infeasible for attackers to decrypt the data without the correct encryption key.
- Key Protection: The encryption keys used by BitLocker, such as the Full Volume Encryption Key (FVEK) and the BitLocker Volume Master Key (VMK), are stored securely and are protected by user authentication credentials, a USB key, or a Trusted Platform Module (TPM). Without the proper key or authentication, recovering the original data becomes nearly impossible.
- On-the-Fly Encryption: BitLocker performs encryption and decryption on-the-fly as data is read from or written to the drive. This means that data is never stored in an unencrypted state on the disk, adding an extra layer of protection. However, it also means that if data becomes corrupted, attempting to recover it directly from the disk might be more challenging.
- Data Consistency: Corrupted data on a BitLocker-encrypted drive may result from issues such as hardware failures, file system errors, or other forms of data corruption. BitLocker is designed to prioritize data consistency and integrity, and as a result, corrupted data might not be recoverable without the correct decryption keys.
- Limited Recovery Options: BitLocker doesn't provide built-in data recovery tools specifically for corrupted files. Recovery options often involve fixing underlying issues causing corruption, restoring from backups (if available), or, in extreme cases, attempting to recover data using specialized data recovery software. However, success in these efforts is not guaranteed and depends on the extent of the corruption.
- Security Features: BitLocker includes security features like secure boot and pre-boot authentication, which make it difficult for unauthorized users to tamper with the system or gain access to the encryption keys. These features add an extra layer of protection but can also complicate data recovery efforts.
Simple Steps to Recover Corrupted Data from Your BitLocker Encrypted Drive
In summary, the difficulty of recovering corrupted data from a BitLocker-encrypted drive stems from the strong encryption, key protection mechanisms, on-the-fly encryption processes, and overall focus on data integrity and security. Users should prioritize regular backups and follow best practices to prevent data corruption, as the emphasis of BitLocker is on data security rather than facilitating data recovery from a corrupted state.
- Identify the Issue: Before diving into recovery, understand the nature of the data corruption. Is it a result of hardware failure, software issues, or accidental deletion? Knowing the root cause will guide your recovery strategy. If the failed hard drive makes any noises or clicks, STOP at this step and don’t power up the drive. Look for professional help.
- Check for Hardware Issues: Sometimes, corruption might be due to problems with the physical drive. Check the drive connections, try using a different USB port or cable, and ensure the drive is recognized by your computer. If there's a hardware fault, fixing it could resolve the corruption.
- Backup Your Encrypted Drive: As a precautionary measure, if you haven't done so already, back up your BitLocker-encrypted drive. This ensures that even if recovery attempts are unsuccessful, you have a copy of your important data.
- Use BitLocker Repair Tools: BitLocker provides built-in repair tools that can be accessed through the BitLocker management interface. Right-click on the encrypted drive, go to 'Manage BitLocker,' and click on 'Repair Drive.' Follow the on-screen instructions to initiate the repair process.
- Restore from Backup: If you have a recent backup, consider restoring your data from it. This is the safest and most reliable way to get back your files, especially if the corruption is extensive.
- Seek Professional Help: If all else fails, it might be time to consult with a professional data recovery service like ACE Data Recovery. These experts have the experience and tools to recover data from severely corrupted drives. While it can be more costly, it's often the last resort for critical data.
Conclusion: Recovering corrupted data from a BitLocker-encrypted drive may seem like a daunting task, but by following these straightforward steps, you increase your chances of success. Remember, prevention is the best cure — regular backups and proactive maintenance can go a long way in safeguarding your digital treasures. Stay calm, be patient, and with a bit of luck, your data will be back in your hands in no time.
